Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 1
Why Vulnerability Assessment is Important in Virtual Environments?
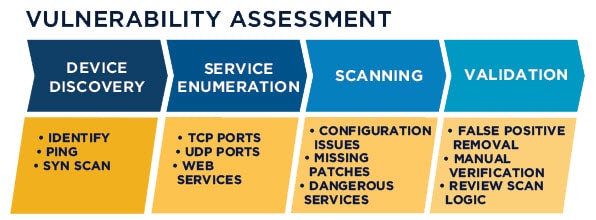
A vulnerability assessment is the process of defining, identifying, classifying and prioritizing vulnerabilities in computer systems, applications and network infrastructures and providing the organization doing the assessment with the necessary knowledge, awareness and risk background to understand the threats to its environment and react appropriately.
In virtual environments, any vulnerability has affect on virtual infrastructure and those who get the service including internal and external services. So at least, any organization should have process to identifying vulnerabilities. Identifying vulnerabilities needs tools in IT infrastructure to scan devices, operating systems and applications and find vulnerabilities (Especially security vulnerabilities).
There is many enterprise and community edition of vulnerability assessment and vulnerability management tools but before talk about scanner and manger, we should talk about different between assessment and management.
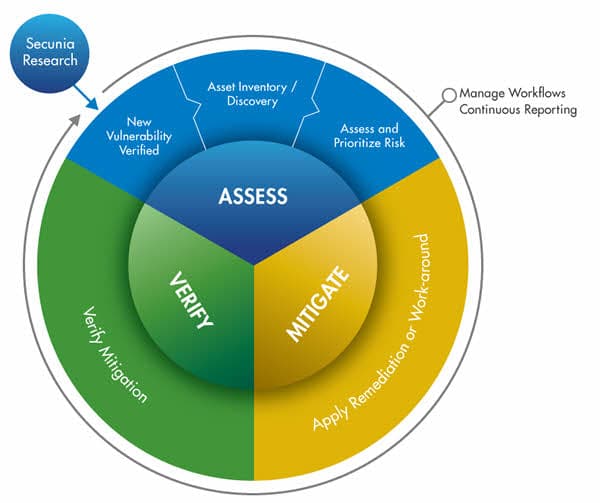
Vulnerability management is the “cyclical practice of identifying, classifying, re-mediating, and mitigating vulnerabilities”, particularly in software. Vulnerability management is integral to computer security and network security, and must not be confused with Vulnerability assessment. Vulnerabilities can be discovered with a vulnerability scanner, which analyzes a computer system in search of known vulnerabilities, such as open ports, insecure software configurations, and susceptibility to malware infections. Unknown vulnerabilities, such as a zero-day, may be found with fuzz testing, which can identify certain kinds of vulnerabilities, such as a buffer overflow with relevant test cases. Such analysis can be facilitated by test automation. In addition, antivirus software capable of heuristic analysis may discover undocumented malware if it finds software behaving suspiciously (such as attempting to overwrite a system file). Correcting vulnerabilities may variously involve the installation of a patch, a change in network security policy, reconfiguration of software, or educating users about social engineering.
What’s OpenVAS (Open Vulnerability Assessment System)
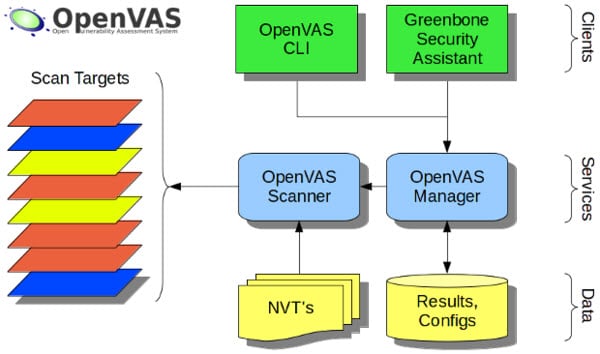
OpenVAS (Open Vulnerability Assessment System, originally known as GNessUs) is a software framework of several services and tools offering vulnerability scanning and vulnerability management. All OpenVAS products are free software, and most components are licensed under the GNU General Public License(GPL). Plugins for OpenVAS are written in the Nessus Attack Scripting Language, NASL.
The framework is part of Greenbone Networks’ commercial vulnerability management solution from which developments are contributed to the Open Source community since 2009. The actual security scanner is accompanied with a regularly updated feed of Network Vulnerability Tests (NVTs), over 50,000 in total.
Yo can find more information about OpenVAS features and structure on the below links:
http://www.openvas.org/software.html
http://www.openvas.org/openvas-nvt-feed.html
https://www.greenbone.net/en/product-architecture/
Also live demo for testing OpenVAS functionality is available at: https://www.greenbone.net/en/live-demo/
How to Install OpenVAS
Today, OpenVAS is available as ISO file to deploying on virtual machine, call it GSM CE (Greenbone Security Manager Community Edition) from now. The ISO file is small and it’s 350 MB. After download, create a virtual machine on VMware ESXi, Hyper-V or Virtual Box with the below specifications at least:
- 2 CPU Cores
- 2 GByte RAM
- At least, 40 GB Disk Space
Note: The GSM Community Edition is a derivate of the GSM ONE and allows a quick and easy option on Windows, Linux or Mac to give the solution a trial. No particular know-how is needed. Greenbone selling GSM (Greenbone Security Manager) as physical appliance with different capabilities.
Load ISO file, power on virtual machine and follow the below instruction to install and configure GSM Community Edition.
Installation Instruction
Follow the below simple steps to install GSM Community Edition (Formerly OpenVAS):
Step 1:
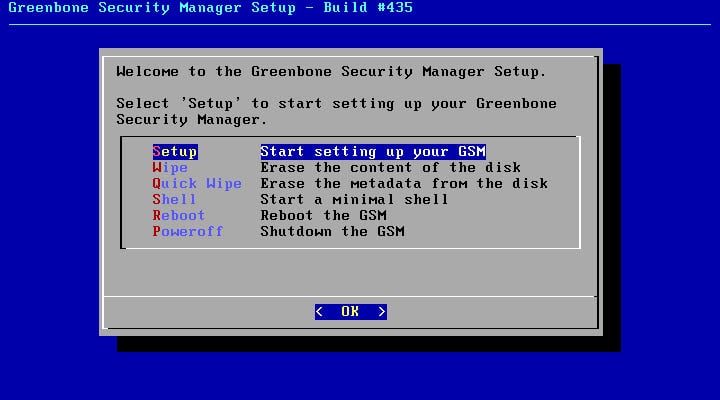
After booting virtual machine by the ISO file, the below menu will be appears, select Setup item and press OK button at the bottom of window.
Step 2:
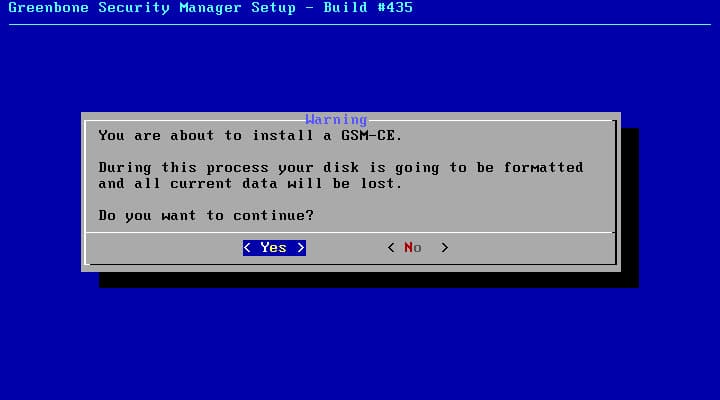
This window shows a message about erasing data on all disks that attached to the virtual machine, there is no other option. Press enter button.
Step 3:
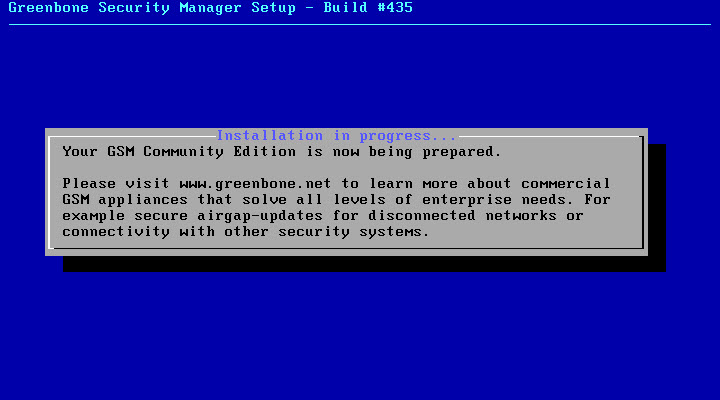
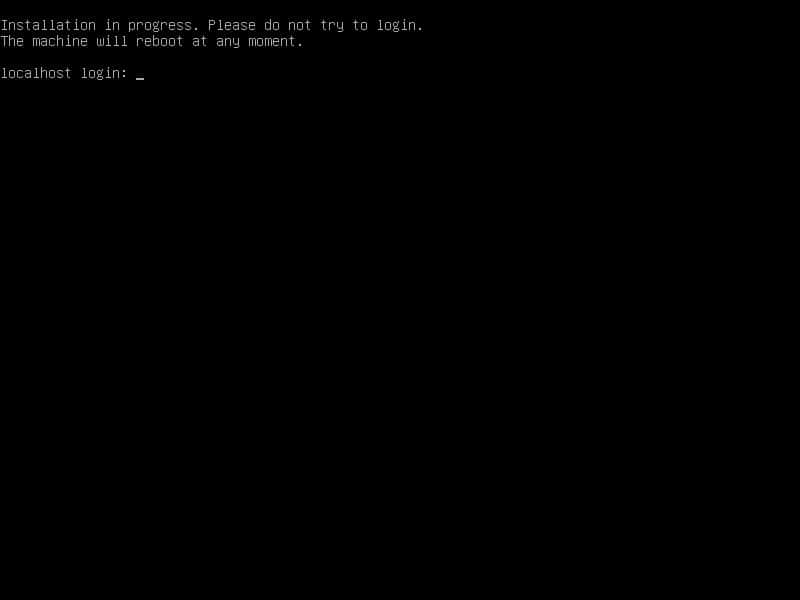
After step 2, installation process has been started and the below message will be appear, installation process takes 5 or 10 minutes:
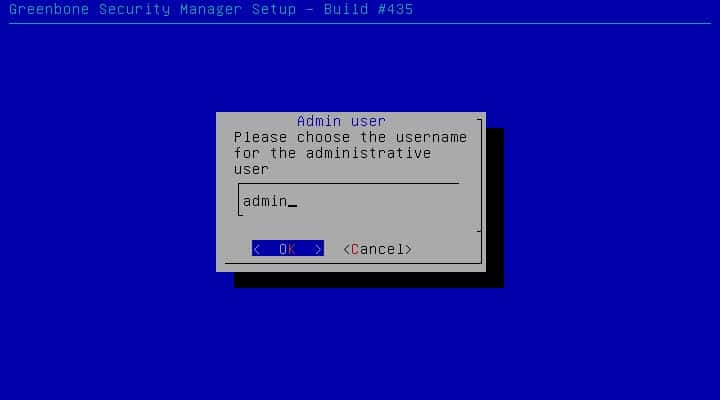
After installation is completed, Installer asks you to define an administrator user, “admin” is a predefined.
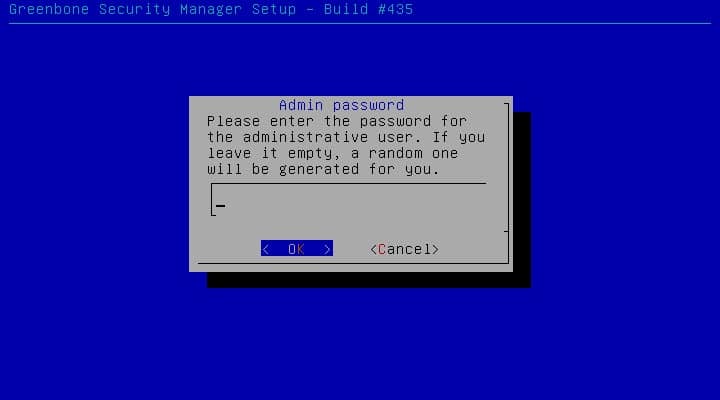
After defining administrator user, enter a password for the user. Unfortunately, the password is clear text.
Note: If you don’t enter password, Installer generates a password randomly.
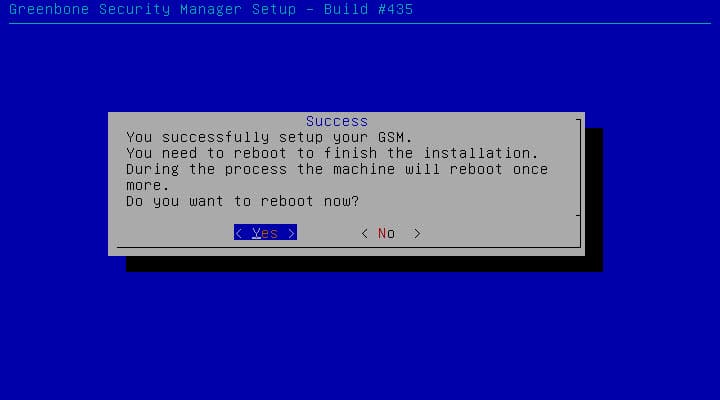
Final Step:
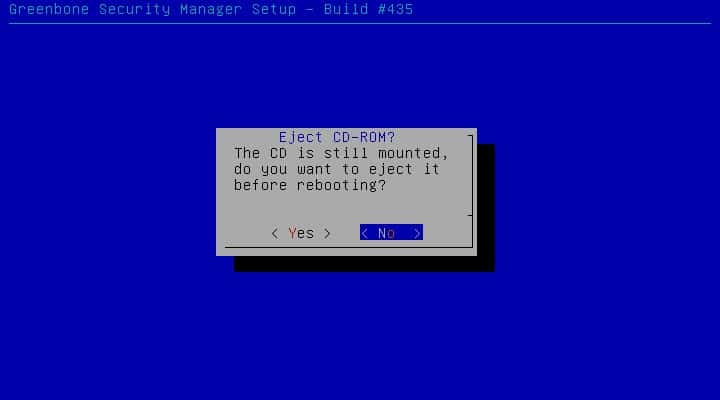
Reboot server and eject installation media.
After first reboot, wait to boot OS and then second reboot.
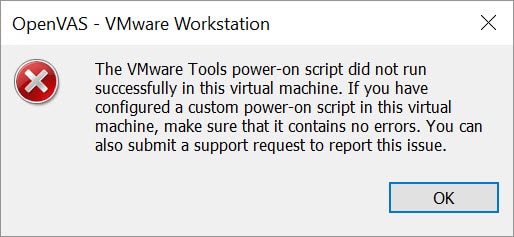
Also you may get the below message on VMware Workstation:
Just click on OK button. There is no issue.
Logon to the server with defined administrator user and password to configure GSM CE.
Configuration
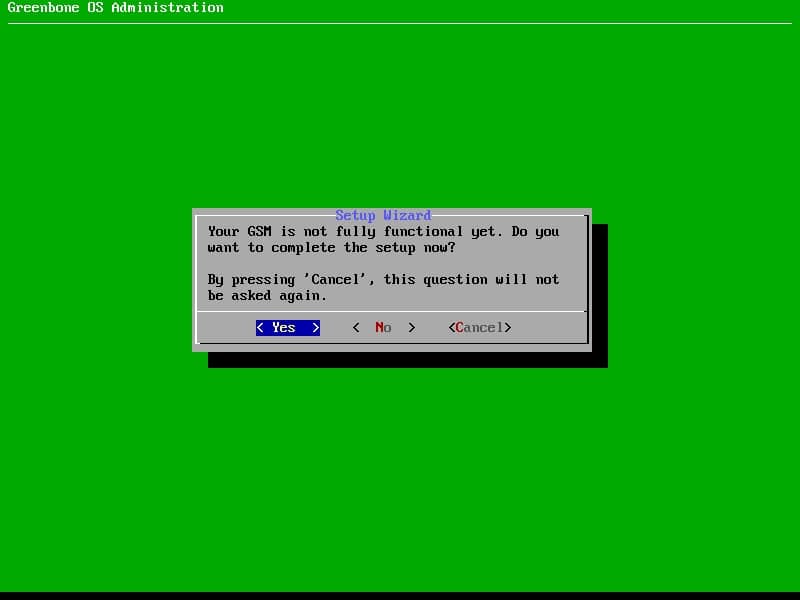
If there was no problem, you will see logon screen after second reboot. The server is not functional yet and some configurations should be defined or change on that.
Greenbone has prepared all configuration in a menu and there is no need to shell normally.
Logon to OS by enter the defined administrator user and password.
After that, Greenbone OS will be redirect you to Greenbone OS Administration. The administration GUI is like the installer GUI and I am sure that it has been created by Dialog.
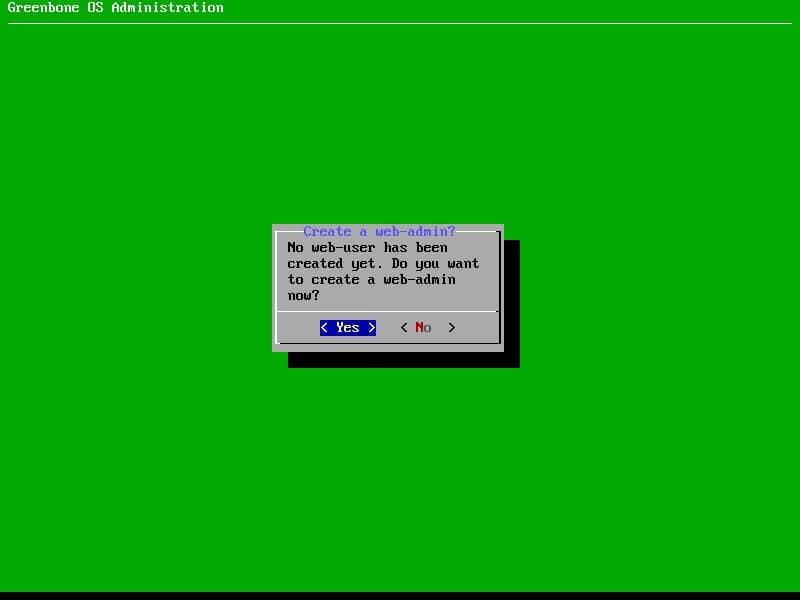
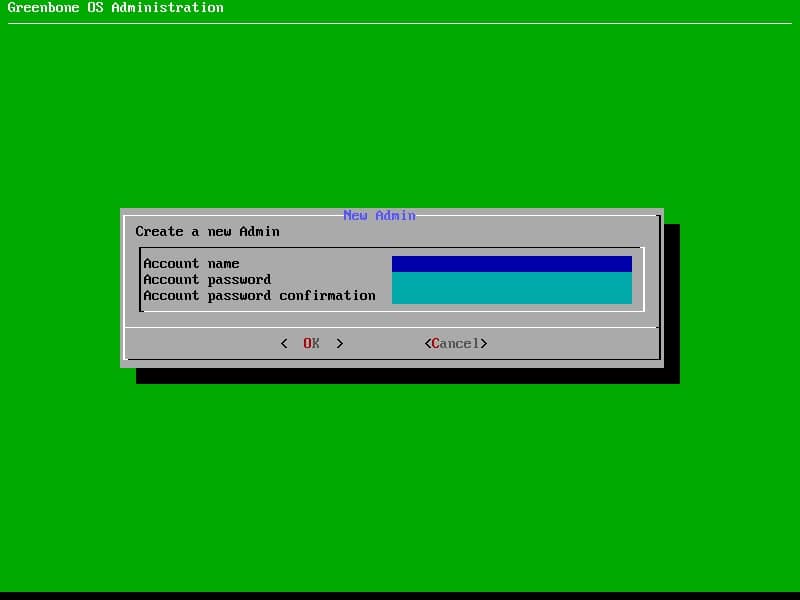
The administrator user that created during installation has no access on web interface so next step is defining new user for accessing to the web interface.
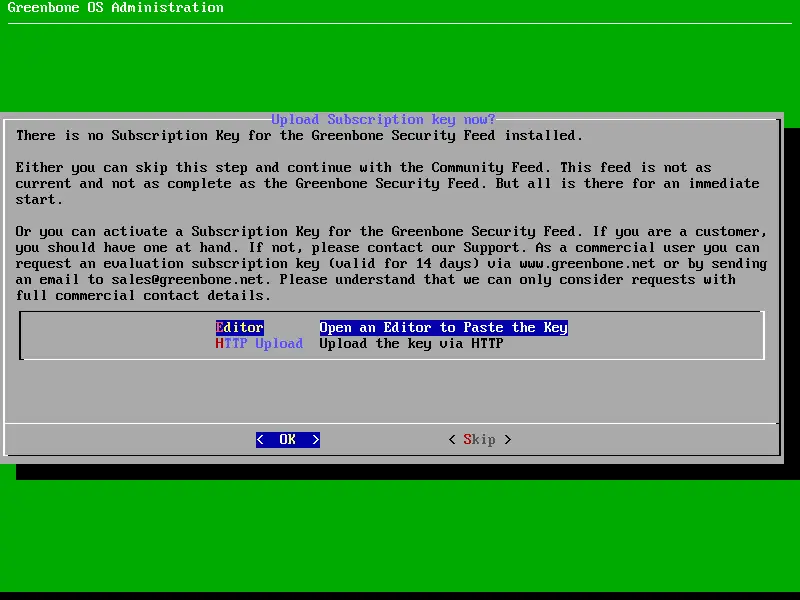
If you have subscription key and you need to support and enterprise version of GSM, follow the below dialog otherwise, skip it.
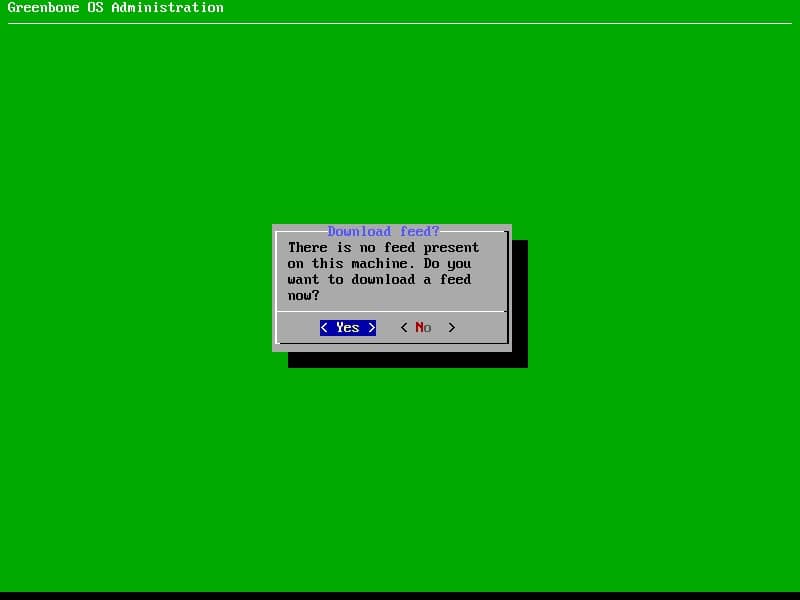
Now, what is feed?
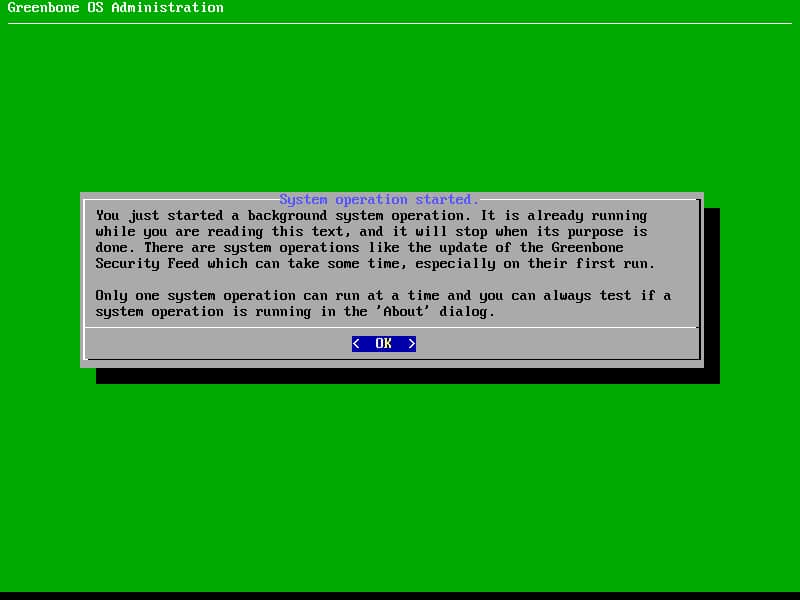
Without a feed you can not do any scans and the SecInfo section remains empty. So the download is highly recommended, but requires internet access.
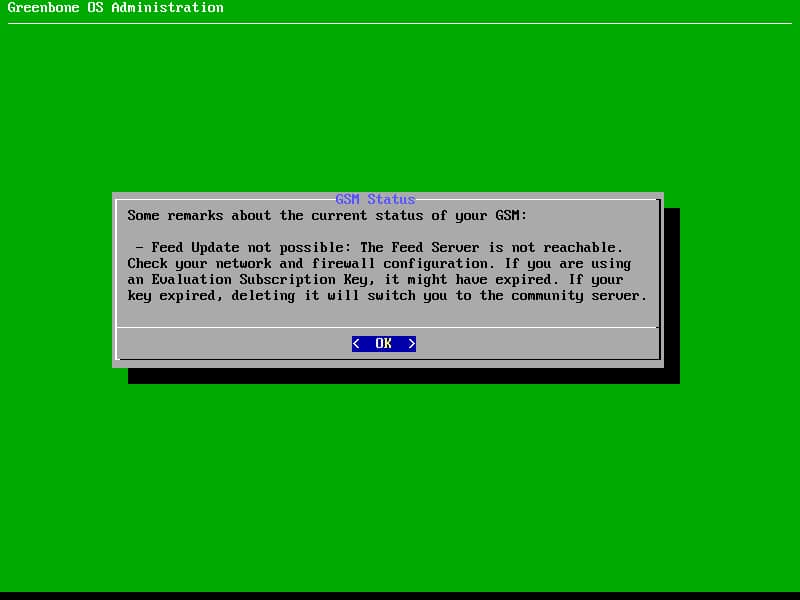
If you faced with the below message, may be there is need to run force update. Force update should be run via shell.
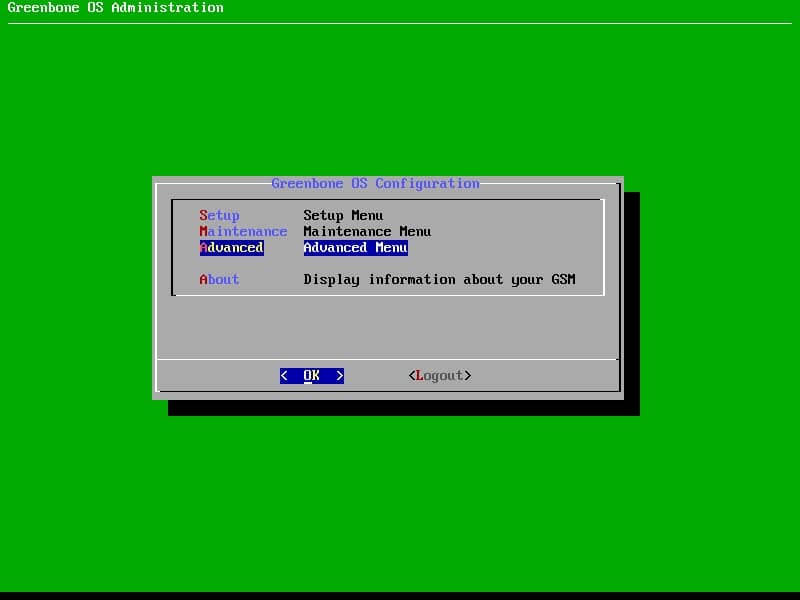
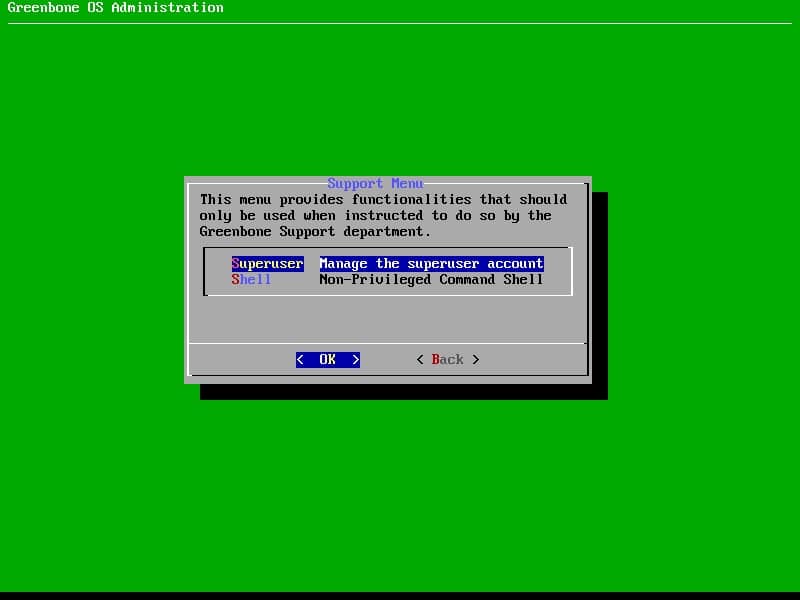
In order to access to the shell, follow the below path of menus:
Main Menu -> Advanced -> Support -> Shell
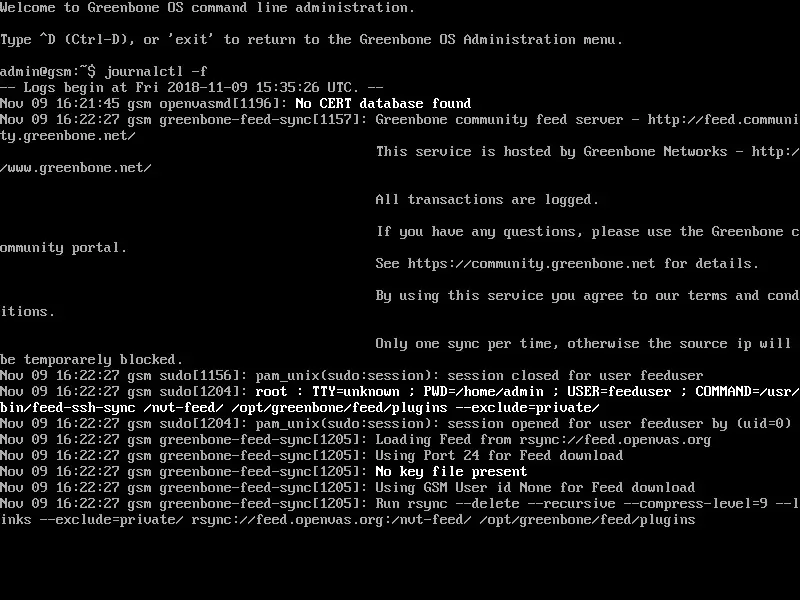
In the loaded shell, type the below command:
journalctl -f
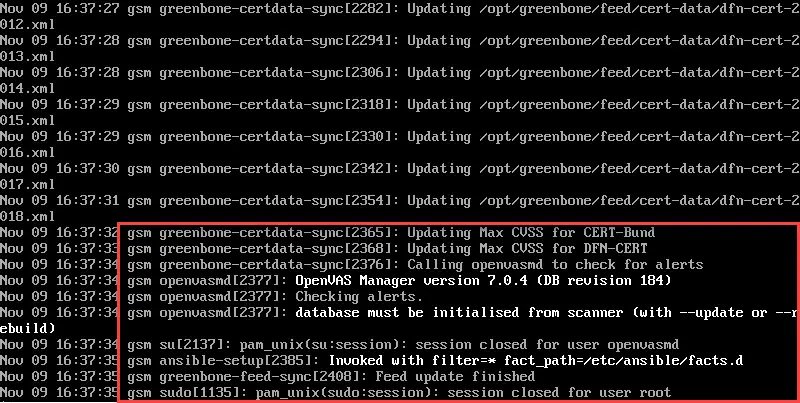
And wait for see some messages like the last screenshot.
About NVT Feed:
Greenbone maintains a public feed of Network Vulnerability Tests (NVTs) for the OpenVAS project, the Greenbone Community Feed. It contains more than 50,000 NVTs, growing on a permanent basis. This feed is configured as the default for the OpenVAS Scanner and relates to the Greenbone Security Feed which is part of the commercial Greenbone Security Manager appliance products.
The Greenbone Community Feed (GCF) and the Greenbone Security Feed (GSF) share the same base set of NVTs. Both are daily updated. This includes immediate availability of “Hot NVTs” which address security problems running fast through the Internet and through the press. Also, improvements contributed by the community will become available without delay.
However, the GCF receives no new NVTs for features for enterprise environments since September 4th 2017. This distinction is regarded an adequate balance between community needs and commercial needs.
For online-synchronisation use the command greenbone-nvt-sync to update your local NVTs with the newest ones from the feed service. This command will download the Greenbone Community Feed unless it is executed in a Greenbone OS environment with a valid subscription key in which case it will download the Greenbone Security Feed.
For offline-updates it is also possible to download the whole Community Feed content as a single archive file (> 25 MByte). However, it is recommended to use the default rsync-based synchronisation routine because it downloads only changes and therefore is tremendously faster after the very first full download.
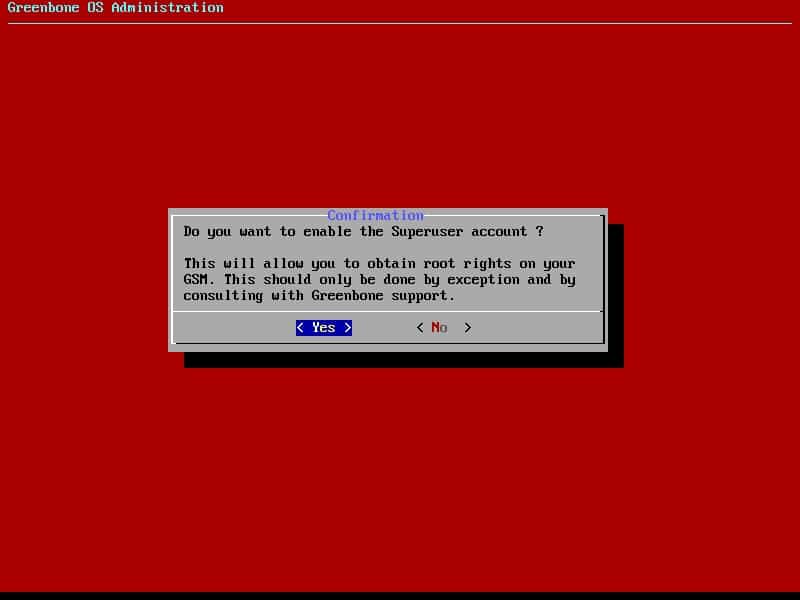
Regarding to update NVTs and other feeds, you need to have access to shell as root. We called the user, superuser.
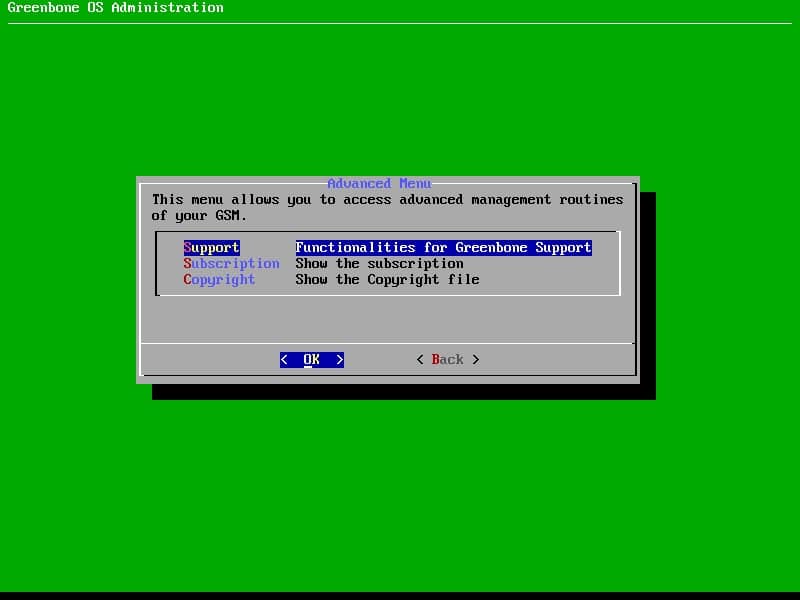
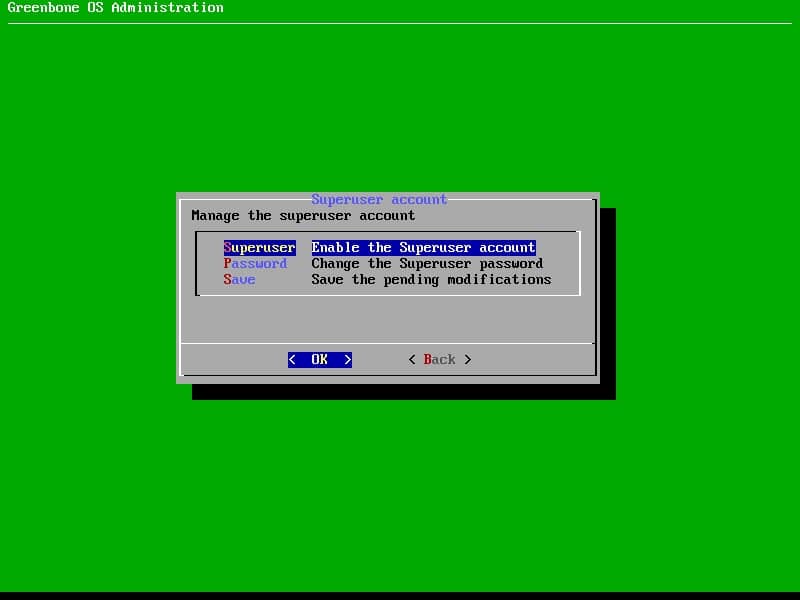
Follow the below path to enabling superuser:
Advanced Menu -> Support -> Superuser -> Superuser (Enable the Superuser account)
Follow the above and change password of superuser also don’t forget Save changes.
After enabling Superuser, logon to shell and run the below command:
su -
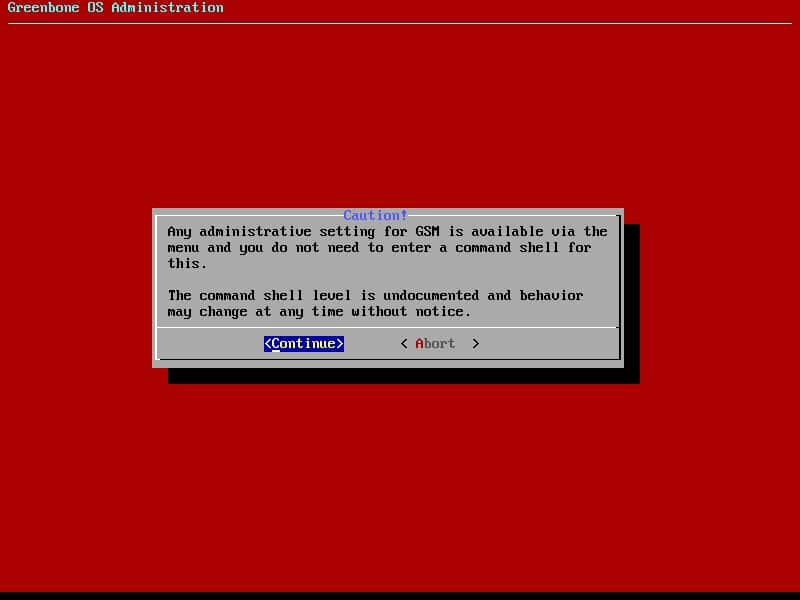
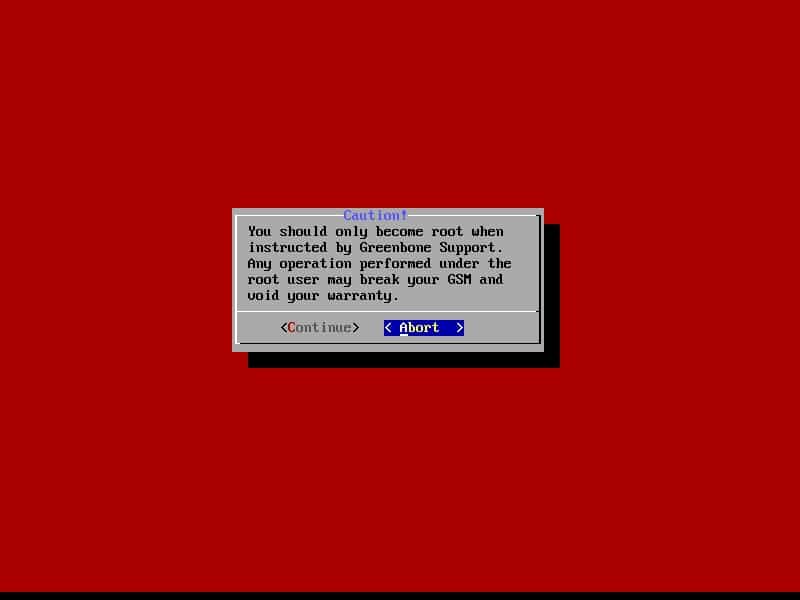
Then enter Superuser’s password. You will see the below warning, choose Continue:
Upload the NVTs compressed file into the server and extract that, then copy all contents to the below location:
/opt/greenbone/feed/plugins/
After that, you be able to update all feeds manually or leave it to update everyday automatically or write the below commands to create a cron to updating all feeds:
- Create a script under /usr/local/bin called feed-update
vi /usr/local/bin/feed-update
- Add the following contents to the file
/usr/sbin/greenbone-nvt-sync /usr/sbin/greenbone-certdata-sync /usr/sbin/greenbone-scapdata-sync /usr/sbin/openvasmd --update --verbose --progress /etc/init.d/openvas-manager restart /etc/init.d/openvas-scanner restart
- Save the file and make it executable
chmod a+x /usr/local/bin/feed-update
- Run the script to make sure it works and that there are no errors
/usr/local/bin/feed-update
- Add the script to cron to run daily
crontab -e
- Add the following contents
1 1 * * * /usr/local/bin/feed-update 1>/dev/null 2>/dev/null
At this state, installation and initial configuration have been done successfully. In the next part of blog post, I’ll show you that how do we can assess ESXi and vCenter servers about security vulnerabilities.
See Also
Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 2
Virtual Environments Vulnerability Assessment By GSM (OpenVAS) – Part 3