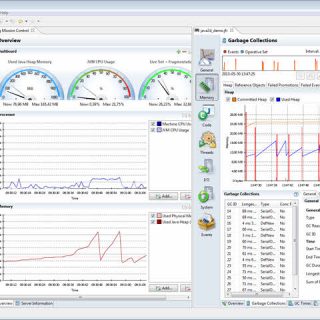
What’s Java Mission Control?
Java programming language is most popular programming languages (Tiobe Index)but Java applications are monster and eating computing resources easily if codes are not optimized and application not profiled. Monitoring Java applications has overhead on a system and in most of scenarios, test environments are different than production environments.