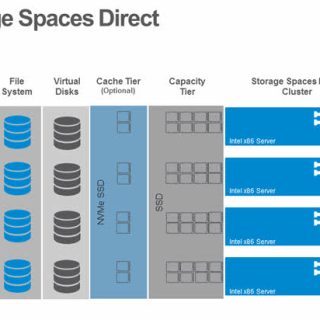
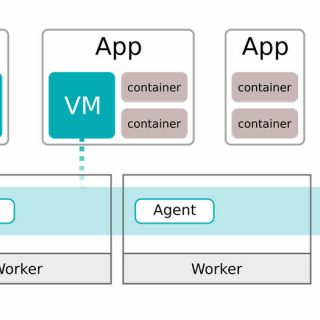
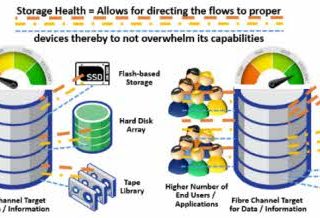
Distributed firewalls, a modern firewall technology, aim to safeguard contemporary data centers and cloud environments. They distinguish themselves from traditional firewalls through various characteristics, such as: dynamic and scalable rule enforcement, which allows for more efficient management and adaptability in rapidly changing network environments. Additionally, distributed firewalls incorporate advanced threat intelligence and machine learning algorithms to detect and mitigate emerging threats in real-time. They also offer enhanced visibility and control, providing administrators with granular insights into network traffic and the ability to enforce policies at a more granular level. Furthermore, distributed firewalls support seamless integration with cloud orchestration platforms, enabling automated and centralized security management across multi-cloud environments. Lastly, these firewalls provide high-performance and low-latency protection, ensuring that network traffic flows smoothly without compromising security. Benefits of Distributed Firewalls They offer a number of benefits over traditional firewalls, including: Use Cases for Distributed Firewalls Can be used in a variety of use cases, including: Samples of Use Cases Here are some specific examples of how distributed firewalls can be used in real-world environments: Here are some samples of distributed firewalls that can be used in infrastructure: These are just a few examples of this type of firewall that can be...