NFTables, The Next Generation of Packet Classification Framework
What is nftables?
Over the years, XTables (IPTables, IP6Tables, ARPTables and EBTables) were using as user-space utility programs for packet filtering in Linux distributions such as Red Hat Enterprise Linux or Ubuntu. Now, Linux vendors are replacing XTables with next generation packet classification framework which called NFTables.
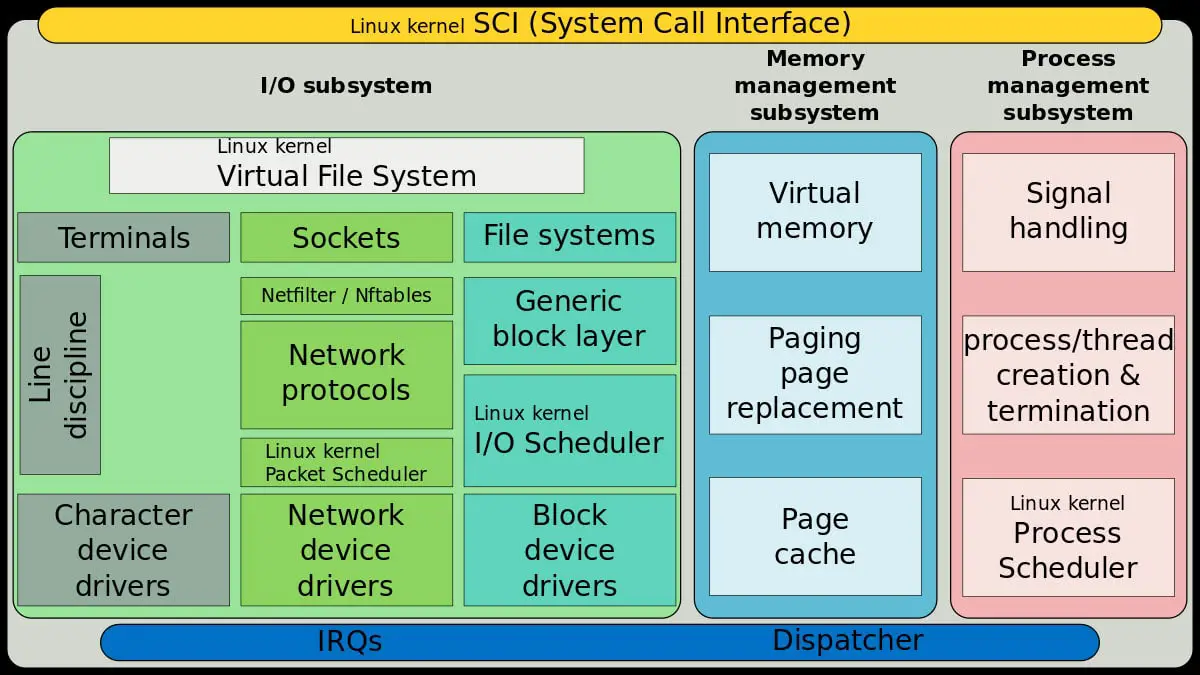
nftables replaces the popular {ip,ip6,arp,eb}tables. This software provides a new in-kernel packet classification framework that is based on a network-specific Virtual Machine (VM) and a new nft user-space command line tool. nftables reuses the existing Netfilter subsystems such as the existing hook infrastructure, the connection tracking system, NAT, user-space queuing and logging subsystem.
Available upstream since Linux kernel 3.13. It supports 3/4 of the existing IPTables features, although it provides new features that you cannot find in IPTables.
nftables is default packet filtering framework in Red Hat Enterprise Linux 8 and firewalld will be use it instead of iptables.
Compare to XTables, Nftables is easier to use and combines all tools of the IPtables framework (e. g. iptables, ip6tables, arptables, etc.) in a single tool. The syntax has also become better and easier, but there is a compatibility layer so you could still use the old IPtables syntax even if filtering is internally done with nftables. Although it basically does the same job as IPtables, its architecture is different. Unlike IPtables, there are no predefined default tables and chains (like filter/NAT or FORWARD/INPUT) in nftables. You can also perform multiple actions in a single rule.
What are Main Features of nftables?
Network-specific VM
the nft command line tool compiles the ruleset into the VM bytecode in netlink format, then it pushes this into the kernel via the nftables Netlink API. When retrieving the ruleset, the VM bytecode in netlink format is decompiled back to its original ruleset representation. So nft behaves both as compiler and decompiler.
High Performance Through Maps and Concatenations
Linear ruleset inspection doesn’t scale up. Using maps and concatenations, you can structure your ruleset to reduce the number of rule inspections to find the final action on the packet to the bare minimum.
Smaller Kernel CodeBase
The intelligence is placed in userspace nft command line tool, which is considerably more complex than iptables in terms of codebase, however, in the midrun, this will potentially allow us to deliver new features by upgrading the userspace command line tool, with no need of kernel upgrades.
Unified and consistent syntax
For every support protocol family, contrary to xtables utilities, that are well-known to be full of inconsistencies.
Examples
Bridge Filtering
Filter on TCP destination port:
nft add rule bridge filter forward ether type ip tcp dport 22 accept
Accept ARP packet:
nft add rule bridge filter forward ether type arp accept
Multiple NATs Using nftables Maps
Thanks to nftables Maps, if you have a previous iptables NAT (destination NAT) rule set like this:
% iptables -t nat -A PREROUTING -p tcp --dport 1000 -j DNAT --to-destination 1.1.1.1:1234 % iptables -t nat -A PREROUTING -p udp --dport 2000 -j DNAT --to-destination 2.2.2.2:2345 % iptables -t nat -A PREROUTING -p tcp --dport 3000 -j DNAT --to-destination 3.3.3.3:3456
It can be easily translated to nftables in a single line:
% nft add rule nat prerouting dnat \
tcp dport map { 1000 : 1.1.1.1, 2000 : 2.2.2.2, 3000 : 3.3.3.3} \
: tcp dport map { 1000 : 1234, 2000 : 2345, 3000 : 3456 }