Demystifying JBD2: The Guardian Angel of Ext4 Filesystems
Data integrity is critical to the digital world. The backbone of this world, filesystems, are essential to the organization and security of this data. Ext4 is the most popular filesystem among them all because of its efficiency and dependability. But the JBD2 journaling layer is a secret weapon that powers its success.
This blog article explores the world of JBD2, including its features, goals, and effects on Ext4. We will make complex topics understandable to readers with different degrees of technical competence by navigating through them in a straightforward and simple manner.
Unveiling the JBD2: A Journaling Revolution
JBD2, short for Journaling Block Device 2, is a journaling layer employed by the Ext4 filesystem and other block devices in the Linux kernel. Its primary function is to ensure data consistency in the wake of unexpected system crashes.
But how does it achieve this seemingly magical feat? Let’s embark on a journey through the fascinating world of journaling.
Understanding the Need for Journaling
Consider penning an intricate article. You take great care to construct each paragraph so that the ideas flow naturally. But your computer goes dark due to an unexpected power failure, so your work is lost. Yes, it is frustrating.
This situation is a fantastic fit for the filesystem domain. Several processes take place while writing data to a disc. Imagine that this procedure is interrupted in the middle by a system crash, leaving the data incorrect. This might result in lost data, damaged files, and a tone of hassles.
JBD2 provides a safety net to stop these kinds of disasters. It keeps a journal, a specific area on the disc that serves as a record of filesystem activities.

The JBD2 Journaling Process: A Step-by-Step Guide
- Transaction Initiation: When you request modifications to the filesystem (e.g., creating a file, editing a document), JBD2 initiates a transaction. This transaction encompasses all the changes to be made.
- Journaling the Changes: Before directly modifying the actual data on the disk, JBD2 meticulously records the entire transaction in the journal. This record includes details about the data being modified, its location, and the expected outcome.
- Data Modification: Once the transaction is safely logged, JBD2 proceeds to perform the actual modifications on the disk. This involves writing the updated data to its designated location.
- Committing the Transaction: After successful data modification, JBD2 marks the transaction as “committed” in the journal. This signifies that the changes have been permanently applied to the filesystem.
This two-step approach, writing to the journal first followed by the actual data, is the essence of journaling. In the event of a system crash, the journal serves as a recovery guide.
The Resurrection of a Filesystem: JBD2 in Action
Let’s go back to the regrettable event of a system failure. When the Ext4 filesystem reboots, it uses the data from the journal to restore its state. JBD2 carefully repeats the logged transactions, restoring consistency and usability to the filesystem.
Consider the essay comparison once more. When you keep a diary, you may retrieve your work even in the event of a power loss by consulting your notes (the journal). JBD2 makes sure that, even in the event of unanticipated events, your priceless data is secure.
JBD2: Beyond Crash Recovery – A Multifaceted Guardian
While crash recovery remains its core functionality, it offers additional benefits:
- Improved Performance: By writing data to the journal first, it allows the actual data modification to happen asynchronously. This optimizes disk access patterns, leading to potentially faster write operations.
- Enhanced Read Safety: Since the journal reflects the intended state of the filesystem, JBD2 can leverage it to verify the consistency of data during read operations. This further safeguards data integrity.
- Reduced Wear and Tear: By minimizing direct writes to the main filesystem area, JBD2 can extend the lifespan of storage devices by reducing wear and tear.
JBD2 Modes: Catering to Diverse Needs
JBD2 offers three operational modes, allowing users to fine-tune its behavior based on their specific requirements:
- data=ordered: This mode prioritizes data consistency, ensuring all data modifications are written to the disk before the transaction is committed to the journal. It offers the highest level of data safety but may come at the cost of slightly slower performance.
- data=journal: This mode strikes a balance between performance and data integrity. Data is first written to the journal and then asynchronously written to the disk. While quicker than ordered mode, it carries a slightly higher risk of data loss in case of a power failure.
- data=writeback: This mode prioritizes performance over data consistency. Data is written directly to the disk, and only the commit record is written to the journal. This offers the fastest write speeds but poses the highest risk of data loss in the event of a crash.
JBD2 in the Real World: A Widely Adopted Hero
JBD2’s effectiveness has made it the default journaling layer for the Ext4 filesystem. Due to its benefits, it’s also employed by other block devices like OCFS2, offering robust data protection and performance in various applications. This includes:
- Desktop and server operating systems: JBD2 ensures data integrity on Linux and other Unix-like systems, safeguarding user files and critical system data.
- Embedded systems: JBD2’s ability to optimize performance and minimize disk wear makes it suitable for resource-constrained embedded systems.
- Solid-state drives (SSDs): With the increasing popularity of SSDs, JBD2’s efficient data management helps optimize write operations and extend SSD lifespan.
Beyond the Basics: Advanced JBD2 Concepts
For those seeking a deeper understanding, here’s a glimpse into some advanced JBD2 concepts:
- Checksum: JBD2 employs checksums to verify data integrity during writes and replays. This further enhances data security.
- Error Correction: JBD2 incorporates mechanisms to handle potential errors during the journaling process, ensuring data consistency even in unforeseen circumstances.
- Journal Tuning: Advanced users can fine-tune the journal size and behavior based on their specific needs and hardware configurations.
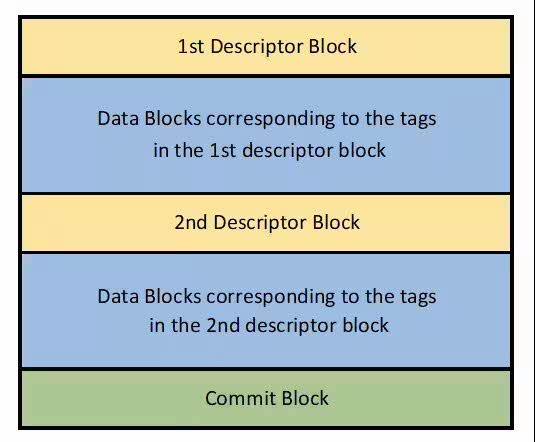
JBD2’s Data Structures: The Inner Workings
JBD2 relies on a set of interconnected data structures to orchestrate the journaling process and maintain data consistency. Understanding these structures is crucial for comprehending the intricate workings of JBD2.
1. Journal Superblock:
- This block serves as the control center of the journal. It stores vital information such as the journal format version, journal size, and checkpoint information.
2. Descriptor Block:
- Each transaction in the journal is represented by a descriptor block. This block contains details about the transaction, including its ID, the number of data blocks associated with it, and flags indicating the transaction state (e.g., ongoing, committed).
3. Data Block:
- These blocks store the actual data being modified during a transaction. They hold the modified content of files, metadata, or other filesystem elements.
4. Commit Block:
- This block marks the completion of a transaction. It signifies that all modifications associated with the transaction have been successfully written to the disk.
5. Revocation Block:
- In rare scenarios, JBD2 might need to undo previously committed changes. Revocation blocks hold information about data blocks that need to be reverted to their previous state in such situations.
6. Transaction List:
- JBD2 maintains three internal transaction lists:
- Running List: Tracks ongoing transactions yet to be committed.
- Commit List: Stores recently committed transactions waiting for replay in case of a crash.
- Checkpoint List: Groups completed transactions, acting as a snapshot for efficient recovery.
Relationships and Interactions:
These data structures work in concert to facilitate journaling operations:
- Transaction Initiation: When a transaction begins, a new descriptor block is created and added to the running list.
- Journaling Changes: Modified data blocks are written to the journal, along with their corresponding information in the descriptor block.
- Transaction Commit: Upon successful completion, the transaction is moved from the running list to the commit list, and a commit block is written to the journal.
- Crash Recovery: In case of a system crash, it replays committed transactions from the commit list and the checkpoint list, utilizing the information stored in the respective data structures to rebuild the filesystem state.
Understanding these data structures provides a deeper appreciation for the meticulous engineering behind JBD2. By efficiently managing these intricate relationships, JBD2 ensures the integrity and consistency of your data, even in the face of unexpected disruptions.
JBD2’s Domain: Operating Systems and Applications
JBD2’s impact extends beyond the Ext4 filesystem, finding its place in various operating systems and applications due to its robust journaling capabilities and potential performance benefits. While its primary use lies with Ext4, it’s crucial to acknowledge its broader presence in the technological landscape.
Operating Systems:
- Linux: As JBD2 serves as the default journaling layer for Ext4, it’s found across most Linux distributions, including Ubuntu, Debian, Fedora, and others. This ensures data integrity for various user applications and system files.
- Unix-like Systems: Other Unix-like operating systems like FreeBSD and NetBSD might also utilize JBD2 with compatible filesystems, providing similar benefits.
Applications:
- Embedded Systems: JBD2’s ability to optimize performance and minimize disk wear makes it suitable for resource-constrained embedded systems. This can be particularly beneficial in devices like routers, network attached storage (NAS), and industrial controllers.
- Database Systems: Some database systems, like SQLite, can leverage JBD2 for journaling their data, potentially enhancing data integrity and recovery capabilities.
- Custom Applications: Developers can employ JBD2 directly within their applications for journaling file operations, offering control over data consistency and recovery mechanisms.
It’s important to note that not all applications explicitly utilize JBD2, as their data storage mechanisms might rely on different approaches. However, its presence within the Linux kernel and compatibility with various filesystems allows it to play a vital role in ensuring data integrity across a diverse range of operating systems and applications.
Furthermore, the specific implementation details and usage of JBD2 might vary depending on the operating system or application in question. Consulting the official documentation for each specific context is recommended for obtaining precise information.
By understanding JBD2’s reach beyond the Ext4 filesystem, we gain a broader perspective on its significance and potential benefits in various technological domains.
Enabling JBD2 on Linux: A Few Caveats
JBD2, as mentioned earlier, is the default journaling layer for the Ext4 filesystem on most Linux distributions. This means no additional enabling steps are typically required for regular users. The Ext4 filesystem automatically leverages JBD2 for journaling operations, ensuring data integrity without manual intervention.
However, there are a few scenarios to consider:
1. Mounting an Existing Ext4 Filesystem:
If you’re mounting an existing Ext4 filesystem that wasn’t formatted with journaling enabled, you cannot activate JBD2 afterward. The filesystem needs to be formatted with the journaling option at creation for JBD2 to be functional.
2. Creating a New Ext4 Filesystem with Disabled Journaling:
While uncommon, it’s technically possible to format an Ext4 filesystem without journaling by specifying the -o noudf option during the mkfs.ext4 command. However, this is strongly discouraged as it removes the crucial data protection layer provided by JBD2.
3. Custom Tuning:
Advanced users might explore fine-tuning JBD2 behavior for specific use cases. This can involve modifying options like the journal size or commit mode through the /proc/fs/jbd2 directory. However, such modifications should be undertaken with caution and a deep understanding of JBD2’s inner workings, as improper configuration can potentially lead to performance issues or data corruption.
Therefore, for most users, JBD2 operates seamlessly in the background, safeguarding their data without any manual intervention. However, it’s essential to be aware of the limitations and potential use cases requiring more advanced knowledge for customization.
Remember, modifying system configurations or kernel parameters can pose risks if not done correctly. Always consult the official documentation and seek guidance from experienced professionals before attempting any advanced JBD2 tuning.
Special Abilities: Beyond the Basics
While ensuring data consistency remains JBD2’s core strength, it possesses some unique capabilities that enhance its overall functionality and cater to specific use cases.
1. Online Resize:
JBD2 allows for resizing Ext4 filesystems while the filesystem is mounted and in use. This eliminates the need to unmount the filesystem and potentially disrupt ongoing operations. JBD2 efficiently handles the resizing process while maintaining data integrity.
2. Fast Recovery:
JBD2’s journaling mechanism enables faster recovery times from system crashes compared to non-journaling filesystems. In the event of a crash, JBD2 only needs to replay the committed transactions from the journal, minimizing the time required to bring the filesystem back online.
3. Checkpointing:
JBD2 utilizes checkpoints to optimize recovery times further. Checkpoints represent points in time where the filesystem state is consistent with the on-disk data. During recovery, JBD2 can start from the most recent checkpoint, replaying only the transactions that occurred after that point, reducing the amount of data to be processed.
4. Wear Leveling:
JBD2 incorporates mechanisms to distribute writes across the entire journaling area, minimizing wear and tear on specific sectors of the storage device. This helps prolong the lifespan of solid-state drives (SSDs) by preventing premature failure due to uneven usage patterns.
5. Error Correction:
It employs checksum to verify data integrity during writes and replays. Additionally, it incorporates mechanisms to handle potential errors that might arise during the journaling process. This multi-layered approach helps safeguard data from corruption even in unforeseen circumstances.
It’s crucial to remember that these special abilities are built upon JBD2’s core journaling functionality. By effectively managing the journaling process, JBD2 unlocks these additional capabilities, offering a comprehensive set of features for data protection, performance optimization, and efficient recovery in various scenarios.
Stepping Out of the Shadows: JBD2 in the Realm of Filesystems
JBD2, while not a standalone filesystem itself, plays a vital role in the data protection and performance landscape. To gain a broader perspective, let’s compare it with other commonly encountered filesystems:
1. Ext2:
- Predecessor of Ext4: Ext2, the predecessor of Ext4, doesn’t utilize journaling. This makes it susceptible to data corruption in case of unexpected system crashes. While offering advantages like simplicity and compatibility with older systems, it lacks the robust data protection capabilities provided by JBD2.
- Use Cases: Ext2 might be considered in scenarios where extreme simplicity and compatibility with legacy hardware are paramount, and data loss risk is minimal.
2. NTFS (Windows):
- Windows Filesystem: NTFS, the default filesystem on Windows systems, utilizes a journaling system similar to JBD2. However, there are some key differences in implementation and features. NTFS offers features like file-level permissions and disk quotas, which are not directly addressed by JBD2.
- Focus: NTFS is optimized for the Windows environment and provides a comprehensive set of features catering to Windows users.
3. FAT32:
- Simple and Lightweight: FAT32 is a simpler and more lightweight filesystem commonly found on flash drives and older storage devices. It lacks journaling and advanced features, making it more susceptible to data corruption and less suitable for critical data storage.
- Use Cases: FAT32 remains relevant in scenarios where compatibility with a wide range of devices and operating systems is crucial, and data storage needs are less demanding.
4. Btrfs:
- Advanced Features: Btrfs is a newer Linux filesystem with several advanced features like built-in snapshotting and self-healing capabilities. While offering a compelling feature set, Btrfs is still considered relatively immature compared to Ext4 and might encounter stability issues in certain scenarios.
- Suitability: Btrfs can be a good choice for users seeking advanced features and willing to accept potential trade-offs in terms of stability and maturity.
5. F2FS (Flash-Friendly):
- Optimized for Flash Storage: F2FS is a Linux filesystem specifically designed for flash storage devices like SSDs. It utilizes wear leveling and garbage collection techniques to optimize performance and lifespan. While offering advantages on SSDs, F2FS might not be as suitable for traditional hard disk drives (HDDs).
- Target Audience: F2FS caters to users prioritizing performance and longevity on flash-based storage devices.
6. XFS:
- High-Performance: XFS excels in speed, especially for large files and parallel operations, making it suitable for HPC and data storage demanding rapid data access.
- Large File Friendly: XFS efficiently handles large files, offering faster read/write speeds compared to other options like Ext4.
- Less User-Friendly: XFS configuration and management can be more complex, requiring a deeper understanding compared to Ext4 or NTFS.
- Limited Features: Lacks functionalities like snapshots or encryption offered by some filesystems, limiting its use in specific scenarios.
- Target Audience: Ideal for users prioritizing raw performance and handling large files, particularly in HPC and data-intensive tasks.
Choosing the Right Filesystem:
The choice of filesystem depends on various factors, including:
- Operating System: Different operating systems have their native filesystems, and selecting a compatible option is essential.
- Storage Device: The type of storage device (HDD or SSD) might influence the choice due to specific optimization needs.
- Performance and Feature Requirements: Users should consider the desired level of performance, data protection, and advanced features like encryption or snapshots.
JBD2, through its integration with Ext4, offers a compelling balance of data protection, performance, and stability. While other filesystems might provide specific advantages in certain scenarios, JBD2 remains a reliable and widely adopted solution for various data storage needs.
File System Comparison: JBD2 vs. Others
| Feature | JBD2 (Ext4) | NTFS (Windows) | FAT32 | Btrfs | F2FS | XFS |
|---|---|---|---|---|---|---|
| Journaling | Yes | Yes | No | Yes | Yes | Yes |
| Data Integrity | High | High | Low | High | High | High |
| Performance | Good | Good | Good | Moderate | Good | High |
| Ease of Use | Good | Moderate | Low | Moderate | Moderate | Moderate |
| Maturity | Mature | Mature | Mature | Newer | Newer | Mature |
| Advanced Features | Limited | More Features | Few | More Features | More Features | Limited |
| Primary Use Case | Linux Desktop/Server | Windows Desktop/Server | Storage Devices | Advanced Users | SSDs | High-Performance Storage |
Additional Notes:
- JBD2 (Ext4) offers a good balance of data protection, performance, and stability for various use cases.
- NTFS is primarily used in Windows environments and provides more features like file-level permissions.
- FAT32 is simple and lightweight but lacks journaling and advanced features.
- Btrfs offers advanced features like snapshots but is still considered relatively new.
- F2FS is optimized for SSDs but may not be as suitable for traditional HDDs.
- XFS is known for its exceptional performance, especially for large files and parallel I/O operations. It’s often used in high-performance computing and data storage applications. However, XFS might not be as widely supported as Ext4 and can be less user-friendly for everyday tasks.
Choosing the right filesystem depends on your specific needs and operating system. Consider factors like:
- Performance requirements: If you prioritize raw speed, XFS could be a good option.
- Data size and type: XFS excels with large files and parallel operations.
- Ease of use: Ext4 and NTFS are generally considered more user-friendly than XFS.
- Operating System compatibility: Choose a filesystem compatible with your operating system.
This expanded table and additional notes offer a more comprehensive comparison of JBD2 (Ext4) with other filesystems, including XFS, allowing you to make informed decisions regarding data storage and management.
Conclusion: The Silent Guardian of Your Data
JBD2, though often unseen, plays a crucial role in safeguarding the digital world. By ensuring data consistency and enabling efficient recovery, it acts as a silent guardian within the Ext4 filesystem. This blog post has delved into the inner workings of JBD2, exploring its functionalities, special abilities, and its place amongst various filesystems.
Understanding JBD2 empowers you to appreciate the intricate mechanisms that protect your valuable data. As technology continues to evolve, JBD2’s robust design and adaptability will likely continue to make it a mainstay in data management, silently ensuring the integrity and safety of your information for years to come.
Remember, this knowledge serves as a foundation for further exploration. If you’re interested in delving deeper, the world of filesystems and data management offers a vast landscape of fascinating concepts and technologies.
Further Reading
Linux Troubleshooting: Mastering the Powerful Tools for Fixing and Optimizing Your System
True Cache vs. Traditional Caching: A Clear Winner Emerges
Direct NFS: The #1 and Ultimate Network File Storage Solution for Oracle Databases
Distributed Firewalls: The #1 Key to a Secure Network
KubeVirt: The Next-Gen Virtualization Solution for Kubernetes – Run Containers and VMs Side-by-Side










