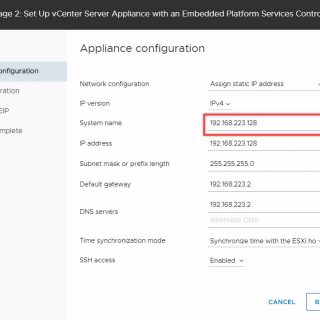
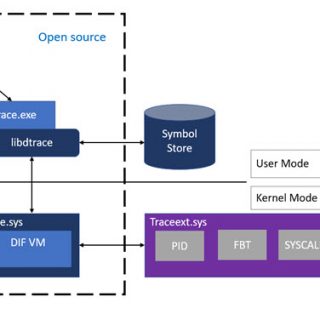
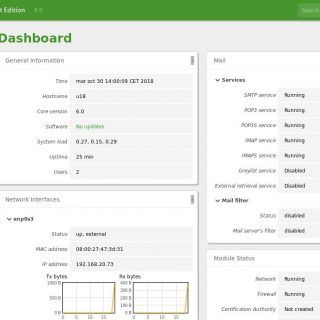
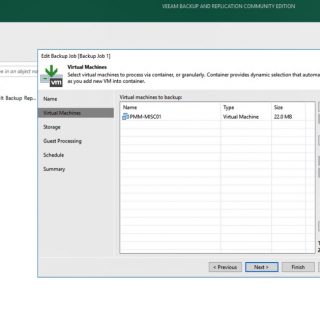
Veeam Backup & Replication Community Edition [formerly known as Veeam Backup Free Edition] is a must have FREE tool for ad-hoc virtual machine (VM) backup, restore and management in VMware vSphere and Microsoft Hyper-V virtual environments. With no agents to deploy, powerful recovery options and VeeamZIP, you get flexibility in options and a reliable solution for important VMs. Whether you are locked in a legacy backup contract or are operating within a tight budget, you’ll find this FREE VM backup software helpful for your daily VM management. Why use Veeam Backup & Replication Community Edition? Even for small infrastructures, virtualization with either VMware ESXi or Hyper-V brings many benefits in terms of savings and ease of administration. Have you ever wanted to back up a VM before making changes to it, clone a VM for testing purposes or make a compressed data archive prior to a VM decommission — just in case? Veeam’s FREE backup tool will cover all your needs! Veeam Backup & Replication Community Edition works perfectly with both standalone ESXi and Hyper-V hosts, as well as with large virtual deployments. Whether you run a test lab or a production environment, it’ll be a perfect match. Are you on a budget or still experimenting with VM backup? Veeam...